
How to find out if a mobile phone is listening, is there a listener on it? How and how to check: whether a cell phone is listening or not?
Safety conversations: Checking if the phone is not listening. Detection of problems.
Navigation
Is it possible to submit a modern person without mobile communication? Older people still remember how much time took the adoption of any decision if the opponent was in another place. Trips, pre-prescribed time and still dozens of difficulties arising from cell phones. No one will argue that mobile phones are the best opening of the last century of simplifying the lives of all social mess.
But where the pros, there and cons - there is always the likelihood that your cell phone is listening. And well, if you communicate with friends on it and decide small home questions, and if you discuss secret information in the conversation process? Voiced what is not intended for third ears and can be used against you? In this article, we will tell you how to solve such a problem, check the phone for the presence of a listener and protect yourself and loved ones.
How to find out if a mobile phone is listening, is there a listener on it?
Listen to a cell phone today not only law enforcement agencies, but literally any person who has certain knowledge and some means. Therefore, if you have something to hide, you provide your financial data by phone or simply do not want you to control - this article for you.
So, the method of first used earlier, but today almost released from everybody - "GSM interception complexes". The fact is that currently GSM channels are encrypted in such a way that there is no technical capabilities without supporting the mobile operator. The method is expensive and heavy in use, so it is used by special services, and then not in all operations.
In fact, it is impossible to determine there is a number of GSM interception complexes, and therefore, if you are hiding, and the level of secrecy is high - do not talk about it by phone. After all, 100% of the safety test method is not.
But now let's move on to numerous programs, with which you can connect the conversations secretly secretly, but for the implementation of this you need access to the phone for 3-5 minutes and install the appropriate program. Such programs act as real spy bugs and allow conversations to any distance, SMS and other information at any distance.
Detect such "bugs" is easier than simple, unless of course they installed the amateur and did not hide the traces of his desistence:
- Go to installed mobile applications and check all installed programs. Those that you personally did not install - boldly remove;
- Reset all settings to factory, plus format the memory card.
We draw attention to the fact that the programs of the telephones wire without operating systems simply do not exist! Now you understand why almost every businessman in his pocket is a telephone that many consider not something that is suitable for communication, but simply rarity.
Lisze programs can enter the phone using:
- Download by link or installing a mobile application;
- Installations using a PC or other mobile device;
- Transfer of reference through MMS;
- Via bluetooth channel;
- By Wi-Fi Channel.
How and how to check: whether a cell phone is listening or not?
In essence, the wiretapping program is divided into two groups:
- When talking, the wiretapping is turned on and all calls are recorded directly into the phone's memory (note that this action is secretive, often and the folder in which conversations are written). Please note that the programs are well compressed information, and the conversation hour is easy to fit in 5-6 MB, accordingly, it is not possible to detect the memory overload. Further, as soon as the phone is in a fairly close contact, the conversations are overwritten on a PC or another phone using WiFi, GPRS, WAP, 3G. It should be borne in mind that at the same time the means from the account transfer account is written off directly from the listening phone, which is clearly displayed at the cost of communication, and it can become a signal to action;
- Conference. Another clever method for listeners of other people's conversations. To do this, at first a conversation comes SMS with the number of the phone of the incoming or outgoing call of the mobile device. Next, the attacker calls back to the room, and becomes the third participant of the conversation. The method is quite complicated and requires a variety of costs, plus the beginning of the conversation is lost, and if the conversation is short, then the attacker gets at the end of the conversation. Therefore, it is extremely rare;
Remember that you are prohibited to listen and write down the calls, and for it is provided for criminal liability. If you have a suspicion that you are listening, you should not continue to use the device before checking the apparatus by specialists.
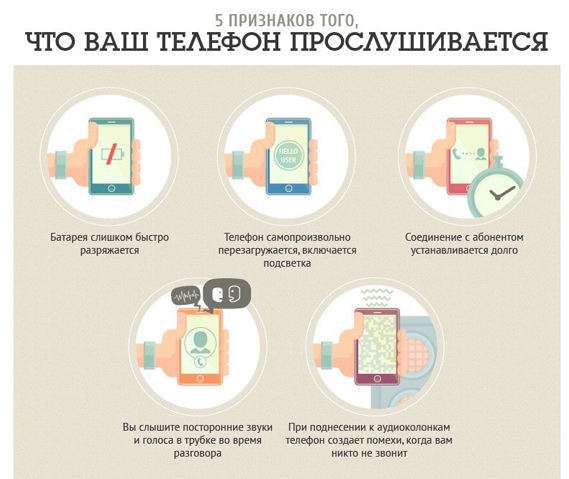
How to detect a listener in your cell phone:
- Unexpectedly, the accumulator began to overheat, especially when calling. If you are watching the movie on your smartphone or play the online game and the battery is basked - this is normal, but the overheating when the call is the correct sign that you need to pay additional attention to the verification. Of course, it can, be launched viral applications, or not closed those that you actively use, but if there are suspicions - the phone is subject to verification;
- You use the phone as usual mode, and the battery stopped coping - requires frequent recharging. Of course, there is a possibility that the battery comes out, but if after buying a new battery, the situation does not change - check for hidden applications;
- Delay when you turn off the phone. It is possible that your phone requires flashing or repair, but there is a possibility that hidden programs are turned off and before turning off and because of this, the phone began to work worse than usual;
- Incredible in the work of the usual smartphone? You are talking on the phone, and in the meantime, the backlit is actively ignited, updates are installed, files are stored, etc.? There is a risk that your phone is controlled remotely. Of course, it is necessary to understand that this is not auto-update, accidentally pressing the keyboard in the ear or cheek, etc. To check the situation when conversations, place on a spelling link and watch the phone's reaction - and then you will surely accept the right decision;
- Presence of extraneous noise. In the case of online listening or conference listeners, there will be noise, noises, tapura, crash;
- In the process of conversation or immediately after completing the conversation, the presence of interference near household appliances. "Bulk" as when sending or receiving notifications;
- With an outgoing call, a stranger appears in the list of operators when choosing a network operator without a logo, but with one or another number. In case of such detection, you may noise without a doubt that your phone is auditioned.
In conclusion, I would like to add that it is better to prevent the problem to "treat". Therefore, do not leave the phone unattended and be attentive to various nuances.

Hello everyone! I came across such a situation, with my husband lived in marriage for 15 years, child 12, began to notice that family relationships were cooled, the husband began to disappear, linger at work. The girlfriend advised one person named Alex, gave me his number 8 968 649 02 03, he set me a listener on his phone, as I knew his location and fully controlled all calls and correspondence, as well as Vatsap and Vaiber. It turns out that His other family, the daughter is growing 6 years old and what he lives with me, only because of his son. Let thousands of deceived wives open their eyes and will recognize whether the second half will know true.
this is verbo:
Go to the LC of your operator and order details on your email,
If there is no SMS confirmation capability, use the aggregator
recommendation Simple
Go to the LC of your operator and order details on your email
Can.
Go to the LC of your operator and order details on your email
Hello! I want to share my story. They lived with her husband for 20 years, met in student years, a mutual sympathy arose, which almost immediately turned into love. For half a year played a wedding, they began their lives from removable apartments (communal) in general, they began to say that spoons and forks began. They graduated from studying, organized a small business, gave birth to 2 wonderful children, lived in the soul. The nebolly business conversion into a rather big company. Bought property and in the city and outside the city, in general, have achieved everything in the life of everything (it would seem to be just happy) But a year ago, the husband seemed to be replaced, became irritable, rude, constantly hid the phone, began to disappear for a few days, (said that supposedly a business trip) I did it believed, I thought it was possible to problems in the company. One day, the husband came home early, went to the shower and left the phone on the table and at that moment SMS came, "Cute we will meet in an hour." I immediately understood the reason for his business trips, but my husband was only dismantled for all my questions about my mistress. Whose problems also had problems with my husband, I advised to put a listener on the phone of her husband. I turned to people who helped learn the whole truth. I could control the whole of my husband , as well as all incoming and outgoing calls. In the end, we divorced with my husband, but I do not regret anything, I think it is better to live knowing the bitter truth than to constantly live in lies.
lol.
has did not help
rememondation
Go to the LC of your operator and order details on your email
Phone is generally not needed and harmful. Registration of a SIM card.
I used to go and bought. Today, SIM cards are drawn up by passport. What is your dog, do you have a phone where I'm and with whom, and what is I talking about? Fuck and who needs global control? Negotiations are auditioned. The phone itself, when you do not speak it, works like a boo. The location of the subscriber at least in cities is determined with an accuracy of several meters. How it's called? What a bastard divorced. Why only a narrow circle know that the whole world currency, including rubles, Jewish? You're typing "Jews", remove on communities and sobble. And they are, at every step. Even on telephone advertising, the Jews will be scanned. Throw a bomb, I do not want, but you will get to the Jew.
Take out batteries with SIM cards and wear separately. Phones are not needed at all. Where and why call?
thank you